Cross Domain Data Hijacking
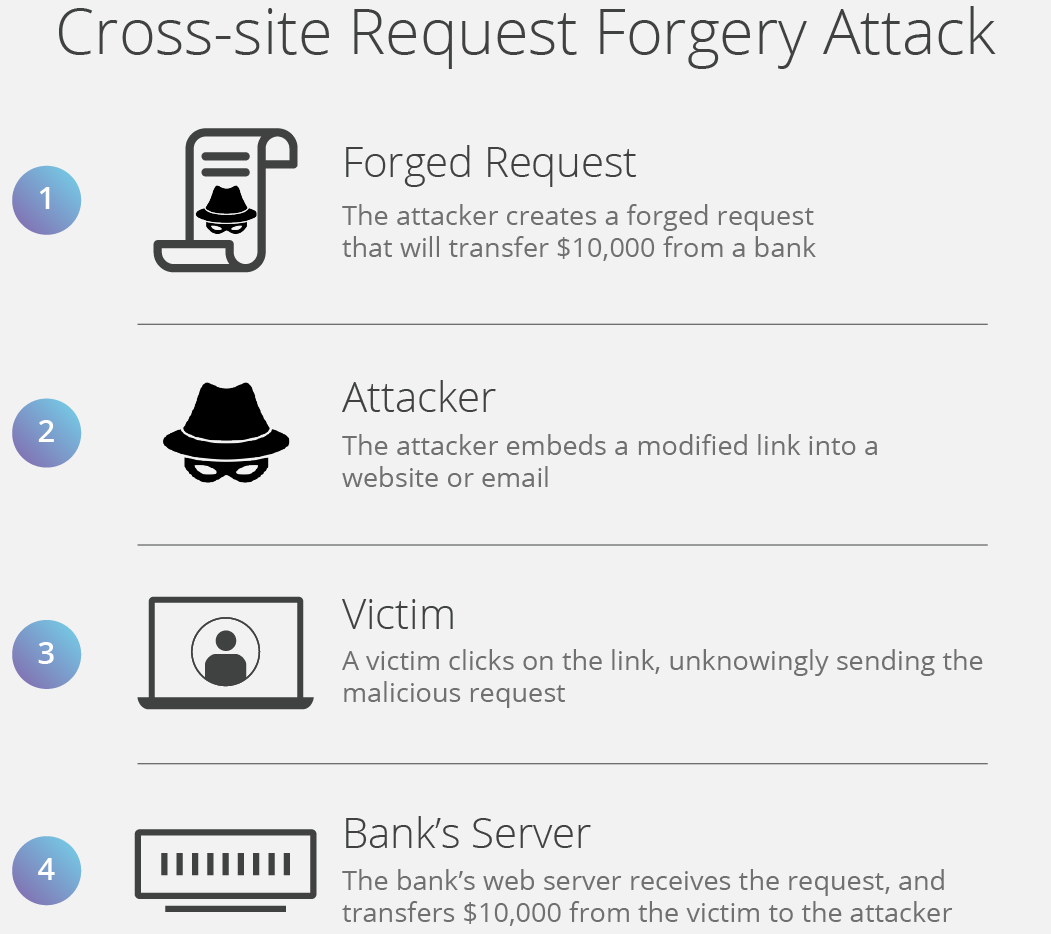
Cross site websocket hijacking also known as cross origin websocket hijacking involves a cross site request forgery csrf vulnerability on a websocket handshake.
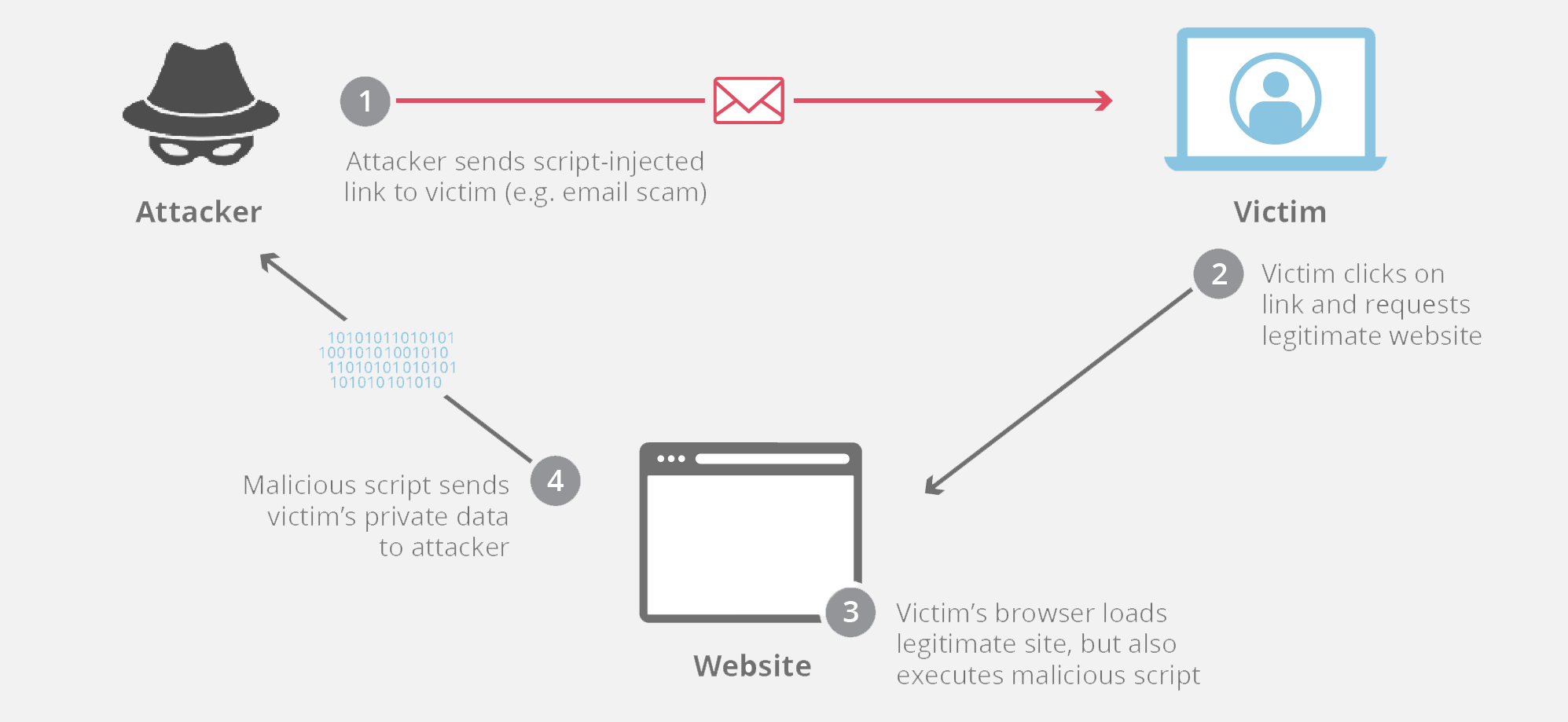
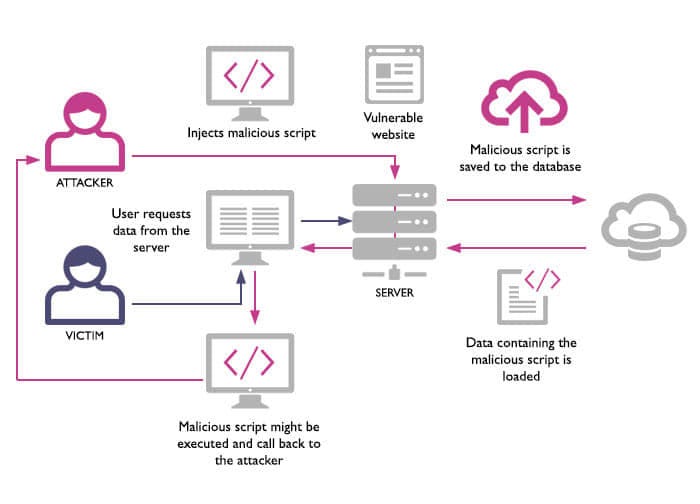
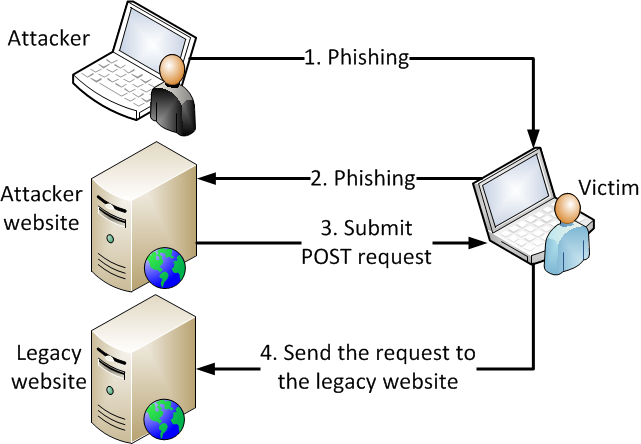
Cross domain data hijacking. If an attacker can create upload a malicious flash swf file or control the top part of any page he can perform an attack known as cross domain data hijacking. This post is going to introduce a new technique that has not been covered previously in other topics that are related to file upload attacks such as unrestricted file upload and file in the hole. Update 3 01 11 2016 title was changed from cross domain data hijacking to cross site content hijacking to reflect the issue better.
Domain hijacking is broadly defined as an attempt to transfer ownership or control of a domain from its rightful owner. This project can be used to provide a proof of concept for. It arises when the websocket.
Cross site content data hijacking xsch poc project license. Click the vsplate go button to launch a demo online 点击vsplate go按钮创建在线环境. The content type of the response doesn t matter.
This project can be used to provide a proof of concept for. Released under agpl see license for more information. Cross site content data hijacking xsch poc project.
This post is going to introduce a new technique that has not been covered previously in other topics that are related to file upload attacks such as unrestricted file upload and file in the hole. This sort of activity often harms the legitimate domain owner. Update 3 01 11 2016 title was changed from cross domain data hijacking to cross site content hijacking to reflect the issue better.
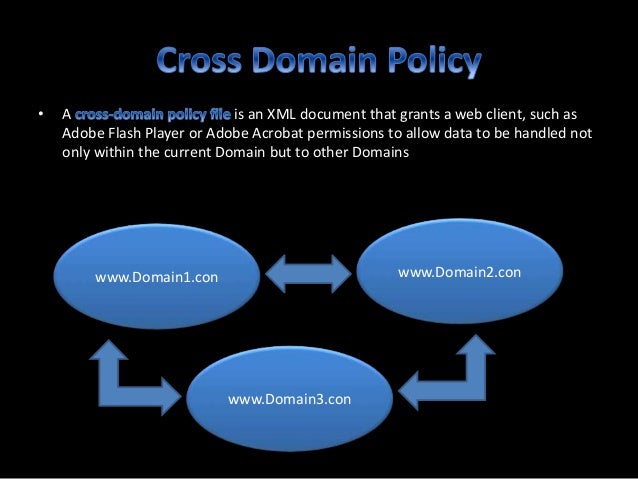
Domain hijacking often involves a fraudulent registrar transfer request or otherwise false change the registration of a domain. The same origin policy controls interactions between two different origins isolating malicious domains to access resources and data cookie token of other domains. Exploiting websites with insecure policy files crossdomain xml or clientaccesspolicy xml by reading their contents.